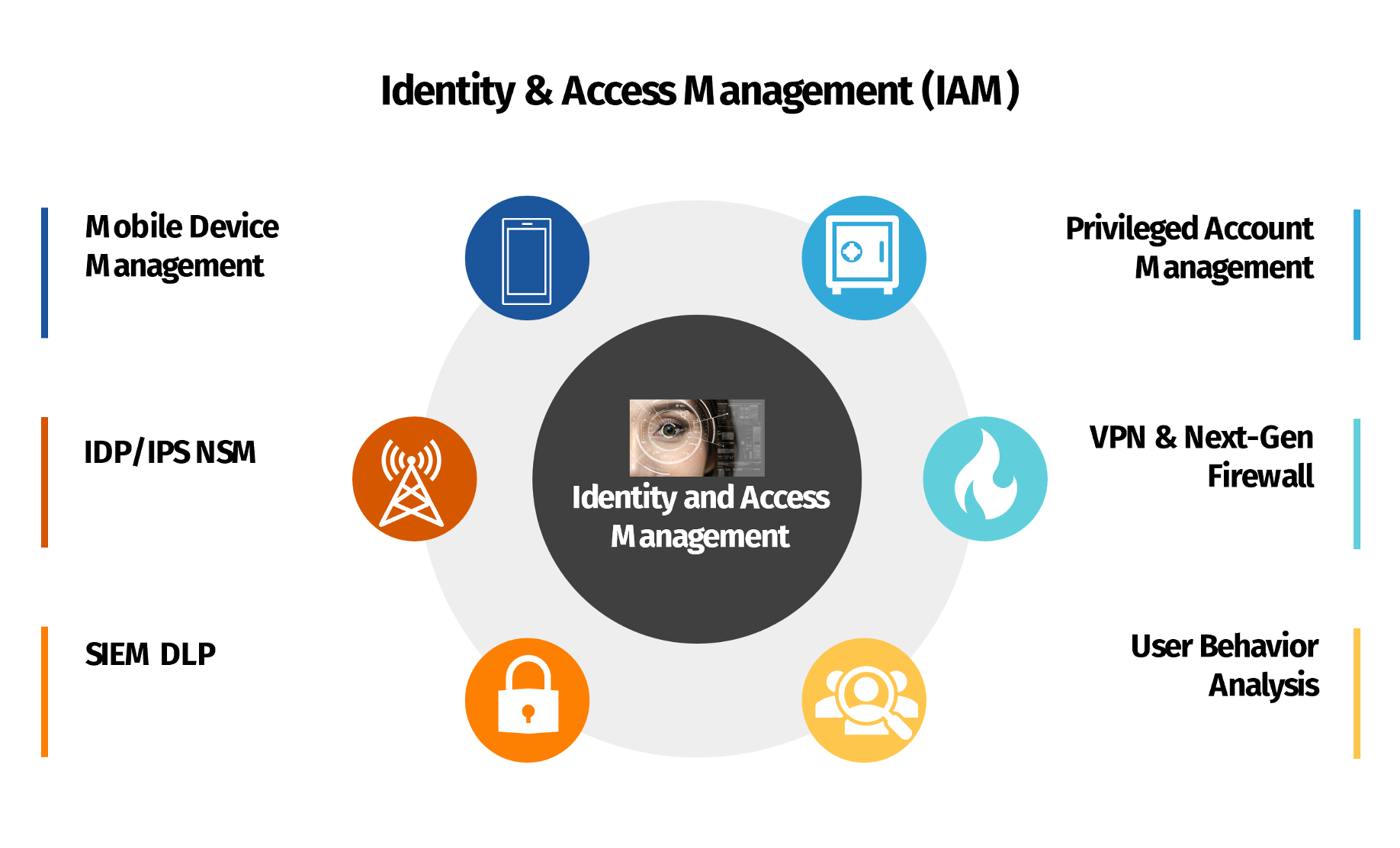
Secure Your Organization with Identity and Access Management (IAM) Services
Effective Identity and Access Management (IAM) is crucial for safeguarding your organization’s data and resources in today’s digital environment. Hum IT’s Security Solutions offers comprehensive IAM services designed to streamline user access, enhance security, and ensure compliance.
Key features include:
- User Authentication: Secure methods, including multi-factor authentication (MFA), to verify user identities.
- Access Control: Granular permissions based on roles and responsibilities, adhering to least privilege principles.
- Identity Governance: Policies for managing user identities throughout their lifecycle, ensuring compliance and reducing risks.
- Single Sign-On (SSO): Simplified access to multiple applications with one set of credentials.
- Audit and Monitoring: Continuous monitoring of access activities and audits to detect and respond to anomalies.
Contact Hum IT’s Security Solutions today to discover how our IAM services can benefit your organization.