Ransomware on Your Mind? Transform Fear into Confidence with these Top Tactics!
 In today’s digital business world, cybersecurity incidents are widespread. In 2023, data breaches reached new highs, exposing over 8.21 Billion records in a year.
In today’s digital business world, cybersecurity incidents are widespread. In 2023, data breaches reached new highs, exposing over 8.21 Billion records in a year.
Such incidents, like data breaches, can severely impact digital businesses. The average cost of a data breach is $4.45 million, often leading to increased costs for customers and making businesses less competitive.
It’s evident that digital business owners must make every effort to enhance the safety and security of their websites, apps, and digital assets.
This brings us to LOTL attacks.
Today, let’s explore LOTL attacks in detail. We’ll tackle the question “What are LOTL attacks?” and delve into the risks they pose to both you and your company. Additionally, we’ll discuss preventive measures to safeguard your cloud services and operating system from potential harm by malicious actors.
Have you heard about the recent LOTL attacks in the news?
Be careful, as they could make you a victim of ransomware!
Stay updated on the recent developments as the LOTL attack evolves into a ransomware threat.
 Living-off-the-Land (LOTL) attacks pose significant risks:
Living-off-the-Land (LOTL) attacks pose significant risks:- Silent and Persistent: Operate quietly, staying hidden for a long time.
- Hard to Detect: Easily bypass regular security, making them tough to spot.
- Stealing Passwords: Grab login details to access sensitive information.
- Moving Undetected: Navigate through networks without getting caught.
- Secretly Taking Data: Transfer stolen data without anyone noticing.
- No Traces Left: Malicious actions leave no traditional evidence.
- Misusing Legit Tools: Turn everyday tools into weapons for harm.
- Supply Chain Risk: Exploit weaknesses in software sources.
What are Living-off-the-Land Attacks?
Living-off-the-land attacks operate by leveraging commonly used tools, turning them into instruments of cyber threat. Among these tools, PowerShell, Windows Management Instrumentation (WMI), and scripting languages stand out as primary vectors for unauthorized use.
LOTL attacks stand out for their ability to operate without leaving any traceable files behind, earning them the moniker of “fileless malware.” The absence of executable files or traditional malware makes it challenging for numerous cybersecurity suites to detect these activities, leaving them oblivious to potentially suspicious events.
Understanding the Mechanics of LOTL Attacks
Living-off-the-land (LOTL) attacks are not new; they’ve been around for a while. Every major operating system has vulnerabilities that make it possible for LOTL attacks to happen. Despite constant efforts, why is it so hard for cybersecurity teams to fully close these security gaps? Let’s explore a few examples to understand the complexity behind it.
Dual-use tools are legitimate computer tools and software that attackers can use in the wrong way.
e.g. Microsoft’s PsExec, WMI, PowerShell
Fileless persistence is a sneaky kind of attack where bad actors can leave harmful stuff on your computer, even after you restart it. It’s called fileless malware, and it’s like hiding bad scripts in the behind-the-scenes part of your computer called the Windows Registry, messing with how things work.
Memory-only Threats are like invisible invaders that execute their harmful code directly in your computer’s memory. This means they leave no traces on your computer’s storage, making them hard to detect. You might hear them called “fileless attacks,” but this term can include attacks that leave a tiny mark on your storage, like those using the Windows registry. An example of a true memory-only attack is the notorious “Mirai” malware that targeted IoT devices. Mirai lived in the device’s memory, so restarting the device cleaned it. Another recent case is the “Wannacry” ransomworm, using the “EternalBlue” exploit. Memory-only attacks are also seen in Point-of-Sale (PoS) malware, where they sneakily access the device’s memory to steal card information.
Non-portable executable file attacks. Some computer files, known as Non-Portable Executable (PE) files, can be tricky. They can infect libraries and tools, like JavaScript or PowerShell, without needing to install typical files you might be familiar with, such as .exe or .dll files. Even seemingly harmless files like .doc files with macros and scripts can be carriers of infection.
This means that tools you usually trust can accidentally carry and spread infections. It’s like a sneaky way for bad stuff to hide in the tools you use every day.
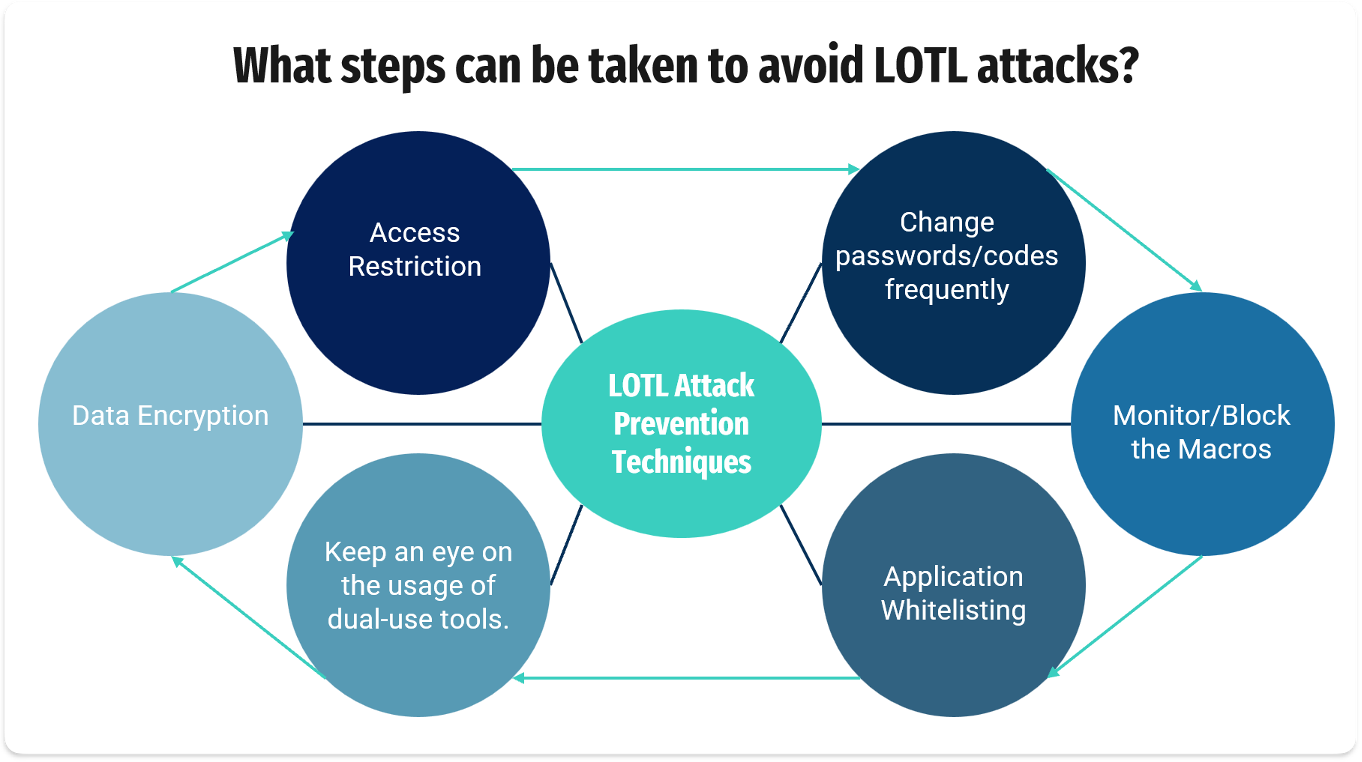
What Cybersecurity Solutions Are Essential to Counter LOTL Attacks
In today’s dynamic digital landscape, the threat of cyber attacks, including the insidious LOTL attacks, is ever-present. As businesses evolve, so do the tactics of malicious actors looking to exploit vulnerabilities and compromise sensitive information.
At Hum IT, we understand the unique challenges organizations face in safeguarding against LOTL attacks. Our tailored cybersecurity solutions are designed to empower you with the proactive defense needed to stay one step ahead of cyber threats.
1. Vulnerability Management
Regularly assess and patch potential weaknesses in your systems to fortify your defenses against LOTL attacks. Our vulnerability management services ensure that your digital infrastructure is resilient to evolving threats.
2. Bug Bounty Programs
Harness the power of ethical hacking through our bug bounty programs. Identify and address vulnerabilities before malicious actors can exploit them in a LOTL attack, creating an additional layer of protection for your organization.
3. Penetration Testing
Simulate real-world attacks to uncover and mitigate potential weaknesses in your cybersecurity posture. Our penetration testing services are a strategic investment in securing your organization against LOTL and other emerging threats.
4. Endpoint Protection
Secure individual devices with robust endpoint protection measures. Prevent malware and other malicious activities associated with LOTL attacks from compromising the integrity of your systems.
5. Threat Intelligence
Stay informed and ahead of LOTL attacks with our advanced threat intelligence solutions. Understand the evolving threat landscape to adapt and fortify your cybersecurity defenses effectively.
6. 24*7 Security Response
Swiftly detect and respond to LOTL attacks with our around-the-clock security response services. Minimize potential damage and downtime by ensuring a proactive and immediate response to emerging threats.
7. Forensic and Ransomware Recovery
In the unfortunate event of a LOTL attack, our forensic analysis services investigate the incident’s extent. Our ransomware recovery solutions efficiently restore affected systems and data, ensuring business continuity.
At Hum IT, we are committed to providing you with a holistic cybersecurity approach tailored to the challenges of today’s digital landscape. Safeguard your organization against LOTL attacks and strengthen your defense with our proven and comprehensive cybersecurity services.
Ready to take the next step in securing your digital future? Contact us today for a personalized consultation and let’s build a resilient defense against LOTL attacks together.
Book a Free Demo Today! and level up your digital security!
Remote work culture refers to the values, beliefs, and behaviours that shape the work environment for employees who work remotely,…